Inside the Fall of XSS.is: Cybercrime’s Biggest Shake-Up
Taking a closer look at a major news story from this summer
👋 Welcome to all our new readers!
If you’re new here, ThreatLink explores monthly how modern attacks exploit technologies like LLMs, third-party cyber risks, and supply chain dependencies. You can browse all our past articles here (Uber Breach and MFA Fatigue, XZ Utils: Infiltrating Open Source Through Social Engineering)
Please support this monthly newsletter by sharing it with your colleagues or liking it (tap on the 💙).
Etienne
A quick break from our series on AI and risk. This summer, one story dominated headlines, and I couldn’t resist digging deeper into it.
What happens?
In late August 2025, European authorities confirmed the arrest of the alleged administrator behind XSS.is, a long-running and influential Russian-language cybercrime forum. The takedown marks a rare but significant disruption of the cybercrime underground, targeting a platform that served as a hub for ransomware operators, data brokers, and malware developers for nearly a decade.
On the surface, XSS.is looked like a typical message board. But for those with access, it was a bustling black market for digital intrusion. With over 50,000 registered users, the forum hosted listings for stolen credentials, ransomware-as-a-service offerings, zero-day exploits, and more. It also functioned as a marketplace for actors in the ransomware supply chain to exchange services, tools, and infrastructure.
Today, if you visit xss.is, you won’t see login prompts or malware listings. You’ll see a law enforcement notice: “This domain has been seized.”
A Coordinated International Operation
According to Europol, the alleged administrator was arrested in Ukraine on a Tuesday in August. This wasn’t a random knock-and-grab.
The French judiciary, working in coordination with Ukrainian and other European partners, obtained surveillance orders for a Jabber messaging server used by the suspect. Intercepted communications pointed to wide-ranging cybercrime activities. According to Paris prosecutors, these messages helped investigators trace more than $7 million in criminal proceeds, including ransomware payments and other illicit gains.
Who Was Behind XSS.is?
While officials have not yet publicly named the suspect, reporting by KrebsOnSecurity points to a 30-year-old Russian-speaking man who operated under the handle “Toha”, among others. Krebs suggests his real name may be Anton Gannadievich Medvedovskiy, originally from Russia but residing in Ukraine for the past several years.
As the administrator of XSS.is, Toha held significant power—he had access to everything shared on the platform. The cybercrime world runs on trust, and users trusted the forum because they trusted the admin, who had built a long-standing reputation in hacking circles. But law enforcement wasn’t the only group interested in unmasking him 😅
In February 2024, the alleged leader of the LockBit ransomware group, “Lockbitsupp,” attempted to learn Toha’s identity—and even reached out to Krebs himself for help. Lockbitsupp claimed Toha’s fake name was Anton Avdeev, though he didn’t explain why he wanted the information.
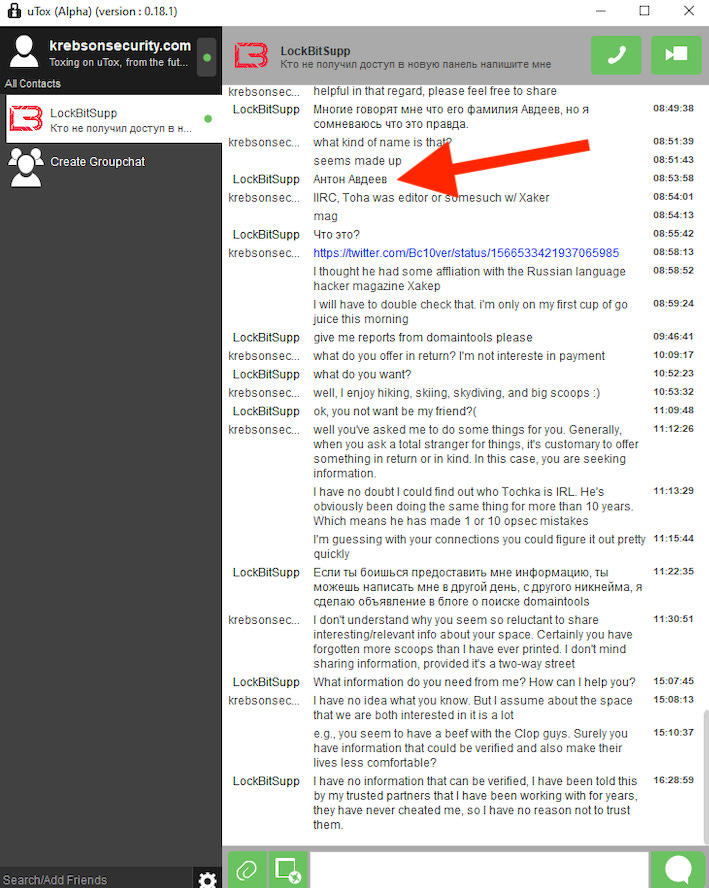
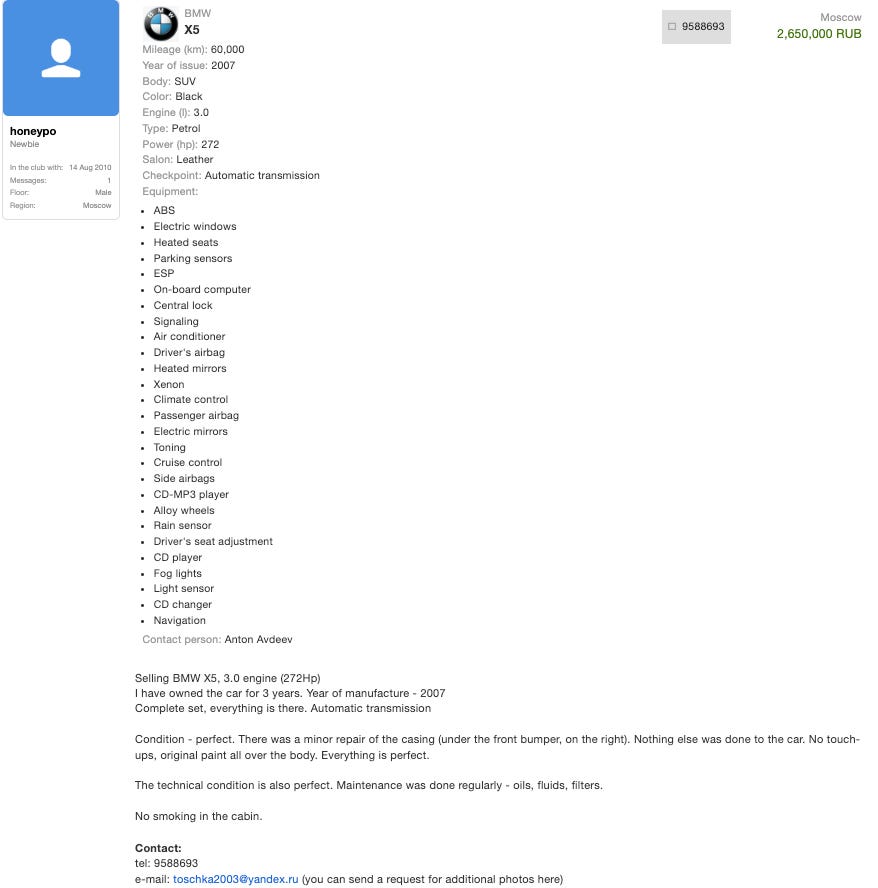
Eventually, Krebs discovered that Toha (link to the email adress toschka2003@yandex.ru) had purchased a BMW X5 in Russia 😅, and had also been using Airbnb for short-term stays.
Even for the greatest criminals, it’s hard to remain completely anonymous or leave no trace.
Why This Forum Mattered
XSS.is was one of the last major enclaves for serious cybercriminals following the shutdown of other forums like RaidForums and Exploit. It was known for strict moderation and high standards, which made it a preferred venue for experienced actors.
It also played a role in real-world attacks. Just weeks before the forum’s seizure, a former U.S. soldier pleaded guilty to a hacking and extortion scheme tied to the sale of stolen data—an operation that had connections to XSS.is activity. (DOJ source)
With the seizure of XSS, law enforcement now has access to a trove of valuable intelligence: user data, transaction logs, private messages. Europol confirmed this information will support ongoing investigations into ransomware groups and other cybercrime operations.
Implications for the Cybercrime Underground
The takedown of XSS.is will cause disruption in the short term, but forums like it often regenerate.
One takeaway shared widely in the cybercrime scene is that Ukrainian and French authorities now possess years’ worth of private messages and logs, not just from the forum, but from the seized Jabber server used by XSS members.
As one user named “GordonBellford” put it on the Exploit forum, following the arrest:
“The myth of the ‘trusted person’ is shattered. The forum is run by strangers. They got everything. Two years of Jabber server logs. Full backup and forum database.”
Source