Uber Breach and MFA Fatigue
Deep Dive into the MFA Fatigue Technique
Welcome to ThreatLink!
I’m Etienne — passionate about tech, cybersecurity and entrepreneurship .
ThreatLink is a monthly newsletter that breaks down real-world cyberattacks involving third-party tools, vendors, and supply chains.
Instead of pointing fingers, we focus on understanding how these breaches happen—analyzing the techniques used and what they reveal.
Each edition covers one major incident with clear, actionable insights for CISOs, security leaders, and the broader cyber community.
The more we share, the stronger we all become.
Uber Breach and MFA Fatigue
In September 2022, Uber suffered a high-impact security breach that exposed critical internal systems. This wasn't the result of sophisticated malware or zero-day exploits, but rather a combination of valid credentials, human error, and social engineering. The entry point? A third-party contractor with privileged access. One of the key techniques used was what we now commonly refer to as "MFA Fatigue."
This post breaks down, step by step, how the attacker infiltrated Uber's environment, what systems were accessed, who the attacker was, and the broader organizational impact of the incident.
The Initial Entry Point
The attacker obtained valid credentials belonging to a third-party contractor working for Uber. This contractor had access to Uber’s internal network via VPN, protected by multi-factor authentication (MFA) using push notifications (Duo Security).
Step-by-Step: How MFA Fatigue Was Used
With the valid credentials in hand, the attacker began a targeted push notification attack, exploiting the way many MFA systems rely on user approval via mobile app:
The attacker started spamming push notifications to the contractor's phone by continuously attempting to log in through Uber’s VPN.
These notifications were sent in rapid succession—dozens, possibly hundreds—causing confusion and disruption, especially since they arrived during the middle of the night.
When the contractor didn’t respond, the attacker escalated the social engineering.
The WhatsApp Message
The attacker obtained the contractor’s personal phone number and sent a message via WhatsApp, impersonating Uber’s IT support team.
The message read something like:
"Hi, this is Uber IT support. We’re experiencing a bug with the login system and need you to accept the MFA notification so it can be reset. Once you accept it, the notifications will stop."
Presented as an urgent, late-night IT support issue, this message lowered the contractor’s guard. Under pressure, and probably fatigued and confused, the contractor approved the next push notification.
At that moment, the attacker was granted full VPN access to Uber's internal network.
Escalation and Lateral Movement
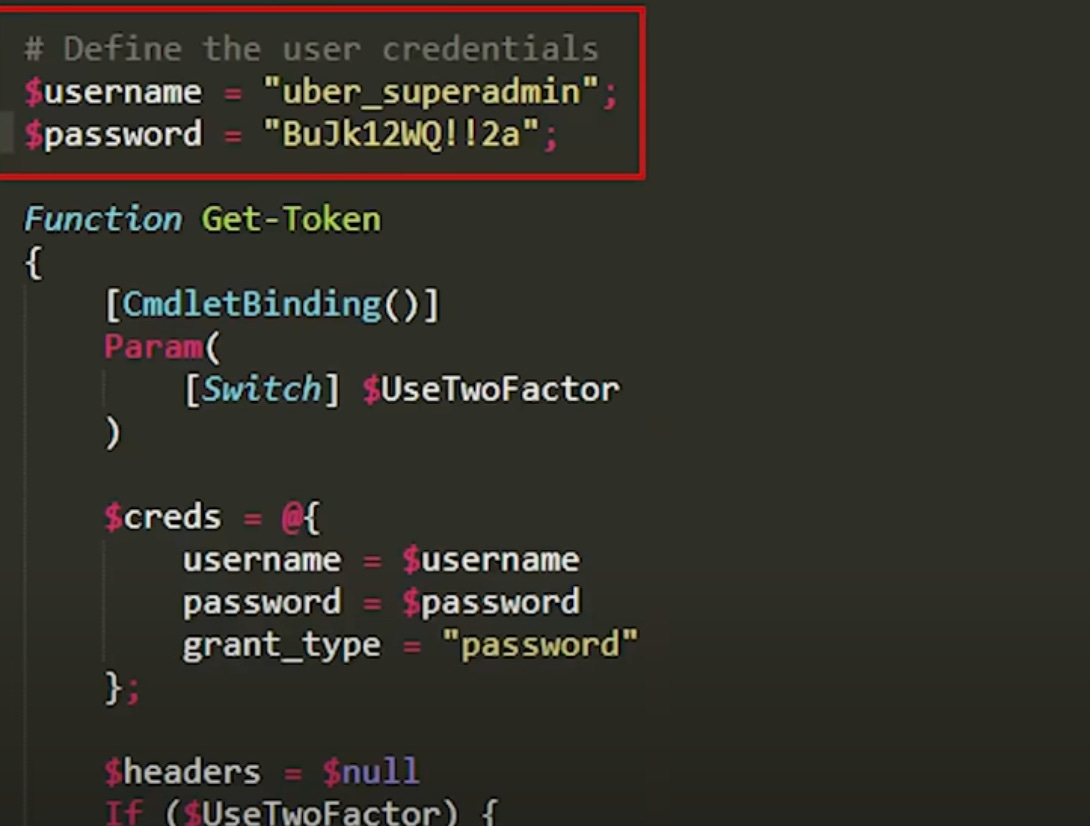
Once inside the VPN, the attacker performed internal reconnaissance and discovered a PowerShell script containing plaintext admin credentials for Thycotic, Uber's privileged access manager.
These credentials enabled the attacker to escalate privileges and gain access to:
Uber's AWS and GCP consoles
BugBounty Program 🥶
Internal Slack channels
GitHub repositories
Engineering systems
Internal financial tools and dashboards
Public Disclosure from Inside
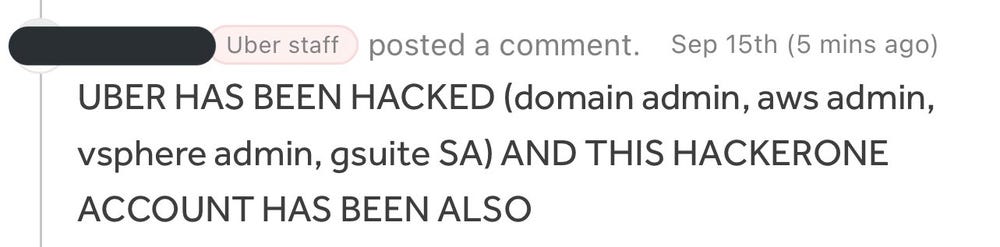
The attacker publicly declared the breach by posting a message on a company-wide Slack channel:
"I am a hacker and Uber has suffered a data breach."
The attacker also left digital messages in internal systems as proof of access.
Who Was the Attacker?
The person behind the breach is believed to be an 18-year-old affiliated with LAPSUS$, a hacking group known for high-profile intrusions at Microsoft, Okta, and Nvidia. In Uber’s case, no data was encrypted, no ransomware was deployed, and no ransom was demanded. The attacker seemed motivated more by notoriety and disruption than by financial gain.
Impact on Uber
Financial Impact
Uber’s stock dropped more than 4% immediately following the announcement. Costs related to forensics, legal support, crisis communication, and remediation were substantial.
Organizational Impact
Slack and GitHub were taken offline temporarily.
Internal credentials and secrets were rotated.
Security teams operated in emergency mode for days to contain and investigate the breach.
Reputational Impact
The breach reignited criticism of Uber’s previous security posture, especially in light of the company’s 2016 breach, which had been covered up at the time.
Final Takeaway
The Uber breach highlights a fundamental issue in modern enterprise security: valid credentials in the wrong hands can be just as dangerous as a vulnerability. It also reinforces the fact that third-party access, combined with a single poor decision under pressure, can expose an entire environment.
This incident wasn’t about technical sophistication—it was about persistence, misconfiguration, and social engineering.
Source